Integrating with webhooks
This guide shows you how to configure, implement and secure webhooks to enable real-time data sync from Prepr CMS to external applications.
Introduction
Webhooks in Prepr CMS let you receive real-time updates for any events.
Whenever a content item, asset, segment, visitor, schema or tag changes, Prepr sends a secure HTTP POST request to your webhook endpoint.
This allows your application to respond to an event triggered in Prepr — whether that’s syncing data, triggering notification or other automation, or keeping your UI in sync with content changes.
Creating a webhook
Before adding a webhook in Prepr, you need to set up your callback endpoint in your application.
The endpoint must use HTTPS and be able to receive POST requests.
Check out the Next.js static website example for example webhook endpoints that check for content_item.changed and content_item.published events.
Webhooks in Prepr send notifications as POST requests and include a JSON payload with Prepr headers and custom headers, if defined in the webhook.
Follow the steps below to add a new webhook.
-
Log in to your Prepr account with a user that has Owner, Admin or Developer rights.
-
Click the icon and choose the Webhooks option.
-
Create a new webhook by clicking the Add webhook button.
-
Add the URL of the endpoint where the notifications will be sent.
-
Select one or more of the supported events to trigger the request.
-
Click the Save and close button.
Check out the list below for additional info you can include in your webhook.
Filtering by model
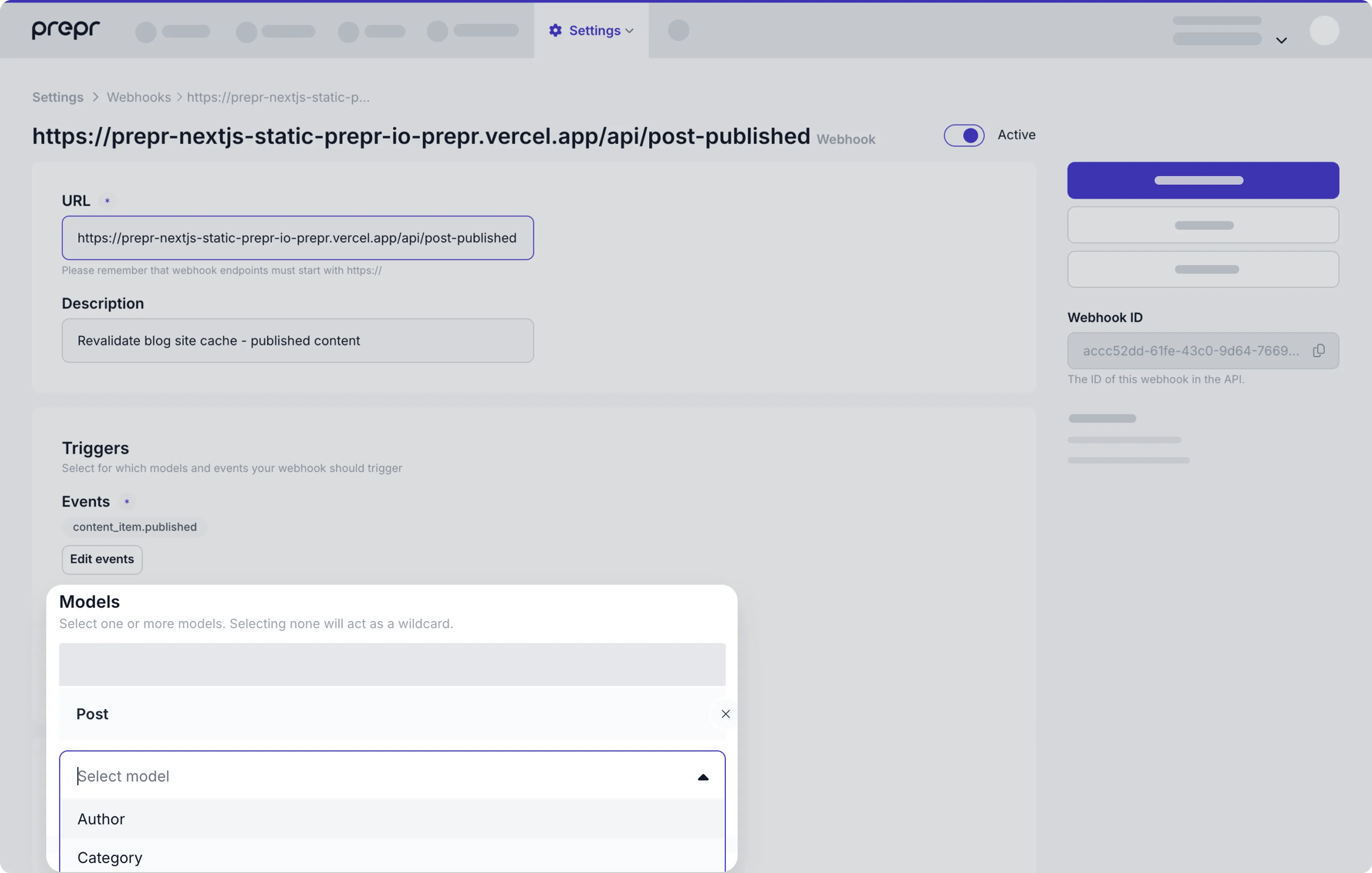
When you select a content item event, you will receive notifications when any content item is created, published, unpublished, changed, or deleted. You can further specify which content items you want to receive notifications from.
Select one or more models to receive webhook events for content items of that specific model.
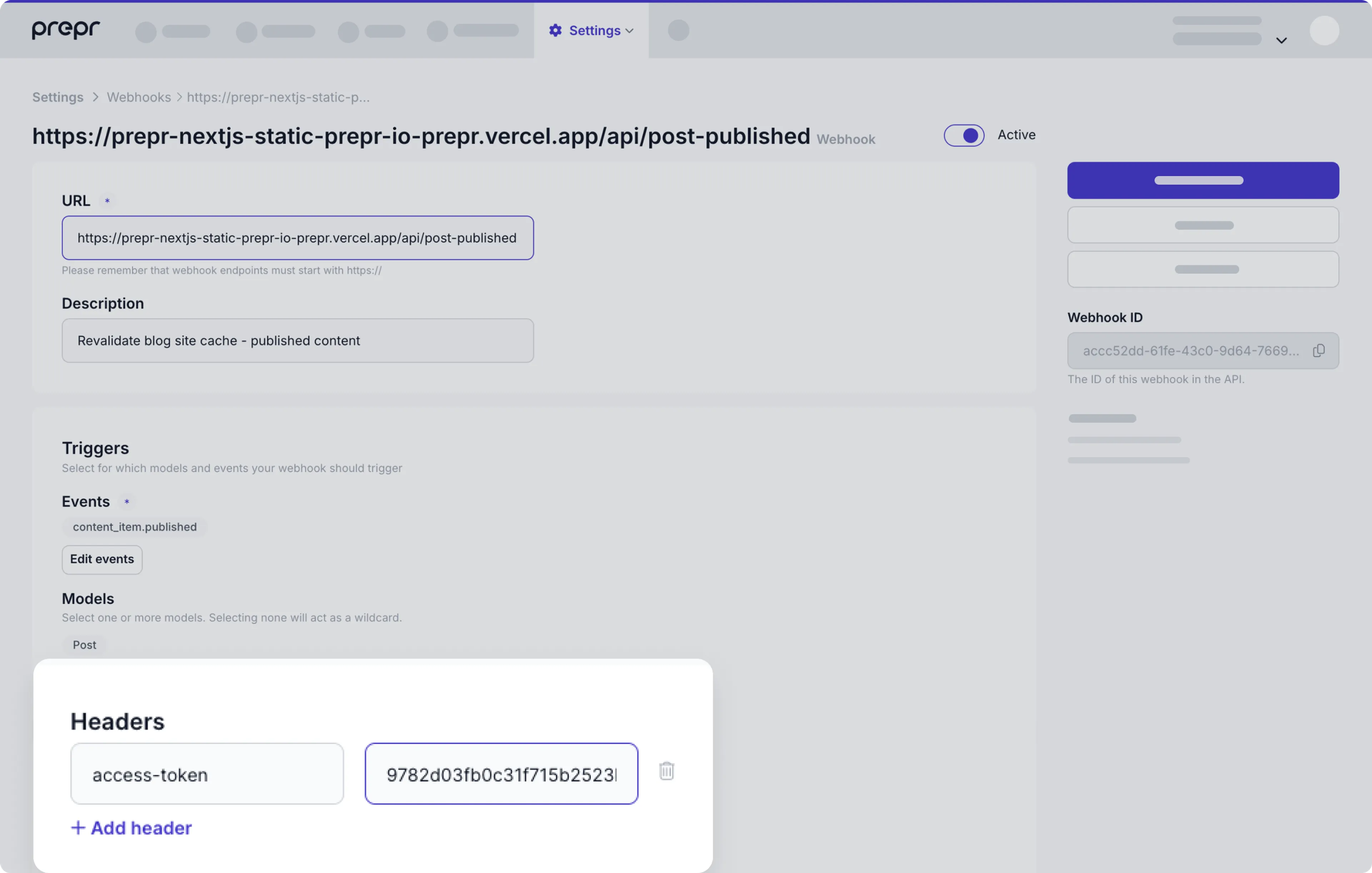
Custom headers
There are some use cases where an application requires some fields to be added in the header of the webhook payload. For example, for access tokens. To add a custom header, enter a header key and value.
Supported events
The events below can be used to trigger a webhook notification. Depending on your plan some options may not be available.
Content item events
| Event Name | Description | Example follow-up action |
|---|---|---|
content_item.published | When a user publishes a content item. | Trigger a static website to rebuild. |
content_item.unpublished | When a content item is moved to Unpublished status. | Remove an article from a Featured list. |
content_item.created | When a new content item is created. | Send a notification to the content production manager. |
content_item.changed | When a content item is changed. | Notify a developer when web app config is changed and might have impact on the front end. |
content_item.deleted | When a content item is moved to the Deleted items list. | Notify a developer when system-related content items are deleted and will impact the front-end. |
content_item.invalidated | When the remote source item used in a content item has changed in the external system. | Trigger the front end to clear the UI cache to track Out of stock products. |
Asset events
| Event Name | Description | Example follow-up action |
|---|---|---|
asset.created | When an image, file or video is initially created in the Media library. (Not yet uploaded) | Send the asset ID to automatically link to a migrated content item. |
asset.uploaded | When an image, file or video is uploaded to the Media library. | Trigger an AI service to generate alt-text. |
asset.changed | When the meta-data of the image, file or video is updated like the title, description or the video thumbnail is changed. | Trigger an AI service to regenerate alt-text. |
asset.deleted | The image, file or video is removed from the Media library. | Send a notification to the content production manager. |
storage_file.deleted | The uploaded file is deleted from storage. | Trigger removal from your own storage. |
cdn_file.deleted | File is purged from the CDN. | Trigger removal from your own CDN. |
Schema events
| Event Name | Definition | Example follow-up action |
|---|---|---|
schema.changed | The data model or field types changed. | Trigger TypeScript regeneration in the front end. |
Segment events
| Event Name | Definition | Example follow-up action |
|---|---|---|
segment.created | When a segment is created. | Create a new corresponding target audience in your CRM. |
segment.changed | When a segment is changed, such as the name, description or conditions. | Sync the updated info to your CRM. |
segment.deleted | When a segment is removed. | Stop all automated workflows associated with this segment. |
Visitor events
| Event Name | Definition | Example follow-up action |
|---|---|---|
person.created | When a new profile is added to the list of web app visitors. | Trigger a Welcome email to the new visitor. |
person.changed | When the visitor data like the email or name is modified. | Sync the updated info to your CRM. |
person.deleted | When a profile is deleted. | Invoke “Right to be Forgotten” protocols for GDPR compliance. |
person.segment.added | When the profile is added to a segment. | Trigger a campaign email the qualifying visitor. |
person.segment.removed | When the profile is removed from a segment. | Revoke a discount code or move them to a different list. |
Tag events
| Event Name | Definition | Example follow-up action |
|---|---|---|
tag.created | When a new tag is added. | Add the tag to the global filter list in the front end. |
tag.changed | A tag name or property is updated. | Bulk-update the display label on all tagged items. |
tag.deleted | A tag is removed. | Remove the tag from the global filter list in the front end. |
Payload examples
The table below outlines the structure of the webhook request, detailing key parameters and their associated data. Each parameter represents an aspect of the event, including metadata.
| Field name | Field type | Description |
|---|---|---|
id | string | The event unique identifier. |
created_on | string | The timestamp in UTC when the event is created. |
event | string | The triggered event, for example content_item.published. |
payload | object | Object with info about the resource that triggered the event. |
performed_by | string | The Prepr user who triggered the event. |
first_published | boolean | A value of true or false is filled when the event is content_item.published. |
locale | string | The language such as en-US is filled when the event is content_item.published, content_item.unpublished or content_item.invalidated. |
The sections below describe the payload for each resource in more detail.
Content item example
The below example request is the payload object when a content_item.published event triggers for a Post model.
{
"id": "75ec2d8c-e5ba-452e-be08-3524af2e1f49",
"created_on": "2025-03-19T14:30:49+00:00",
"changed_on": "2025-05-28T09:01:45+00:00",
"label": "Publication",
"read_time": {
"en-US": 2,
"nl-NL": 2
},
"publish_on": {
"en-US": "2025-05-28T09:01:00+00:00",
"nl-NL": "2025-02-19T12:33:00+00:00"
},
"slug": {
"nl-NL": "de-top-5-mythes-over-autoleasing-ontkracht",
"en-US": "the-top-5-myths-about-car-leasing-debunked"
},
"model": {
"id": "4a8b8f49-b5cd-412f-97e0-5b04a072688d",
"body_singular": "Post",
"body_plural": "Posts"
}
}| Field name | Field type | Description |
|---|---|---|
id | string | The content item unique identifier. |
created_on | string | The timestamp in UTC when the item is created. |
changed_on | string | The timestamp in UTC when the item is changed. |
label | string | Type of resource. For content items, this value is Publication. |
read-time.{locale} | integer | Values are listed for each locale, for example en-US. The calculated time a user reads an article in minutes. |
publish_on.{locale} | string | Values are listed for each locale, for example en-US. The timestamp in UTC when the item is published. |
slug.{locale} | string | Values are listed for each locale, for example en-US. The slug value of the content item, if applicable. |
model.id | string | The internal id of the model. |
model.body_singular | string | The singular name of the model, for example Post. |
model.body_plural | string | The plural name of the model, for example Posts. |
Asset example
The below example request is the payload for an asset.changed event.
{
"id": "c8580913-bbac-4309-9f74-95a6835930b8",
"created_on": "2025-03-19T16:01:14+00:00",
"changed_on": "2025-05-27T15:23:33+00:00",
"label": "Photo",
"name": "bmw",
"body": "",
"author": "",
"status": null,
"replaceable": true,
"reference_id": "b773b7b3-97ce-40c3-ae1f-b1369d0516e1",
"reference": null,
"original_name": "img",
"mime_type": "image/png",
"extension": "png",
"height": 250,
"width": 496
}| Field name | Field type | Description |
|---|---|---|
id | string | The asset unique identifier. |
created_on | string | The timestamp in UTC when the asset is created. |
changed_on | string | The timestamp in UTC when the asset is changed. |
label | string | Type of resource. For assets, this value is Photo, Video or Document. |
name | string | The name of the asset. |
body | string | Additional information about the asset. |
author | string | The person who created the asset such as the photographer. |
reference_id | string | The external id of the asset. |
Segments example
The below example request is the payload for a segments.deleted event.
{
"id": "sgm_5g4820qaz70",
"created_on": "2025-05-28T08:52:19+00:00",
"changed_on": "2025-05-28T08:52:19+00:00",
"synced_on": "2025-05-28T08:52:19+00:00",
"label": "Segment",
"body": "New segment",
"description": null,
"reference_id": "new-segment",
"query": {
"conditions": [
{
"type": "event",
"event_name": "View",
"result": true
}
]
},
"mode": 2,
"count": null
}| Field name | Field type | Description |
|---|---|---|
id | string | The segment unique identifier. |
created_on | string | The timestamp in UTC when the segment is created. |
changed_on | string | The timestamp in UTC when the segment is changed. |
label | string | Type of resource. For segments, this value is Segment. |
body | string | The name of the segment as it’s displayed in the CMS. |
reference_id | string | An external id for the segment. This value can be used to identify the segment in an external CRM system, if applicable. |
query.conditions | array | A list of condition objects for this segment. The object fields depend on the condition options saved for this segment. For a complete list, check out the segments doc. |
Visitor example
The below example request is the payload for a person.changed event.
{
"id": "3b0e2f5e-5b06-4563-828d-13ce49252672",
"created_on": "2024-08-23T07:20:45+00:00",
"changed_on": "2025-05-27T15:48:20+00:00",
"last_seen": "2024-08-23T07:20:45+00:00",
"label": "Person",
"reference_id": null,
"first_name": "Braylen",
"last_name": "Nash",
"full_name": "Braylen Nash"
}| Field name | Field type | Description |
|---|---|---|
id | string | The visitor unique identifier. |
created_on | string | The timestamp in UTC when the visitor is created. |
changed_on | string | The timestamp in UTC when the visitor is changed. |
label | string | Type of resource. For visitors, this value is Person. |
full-name | string | The full name of the visitor. For a full list of available visitor characteristics, checkout the managing visitors guide. |
Tag example
The below example request is the payload for a tag.created event.
{
"id": "c921ef1e-b8e5-4e8a-8cfa-2914665c3bf1",
"created_on": "2025-09-03T12:40:49+00:00",
"changed_on": "2025-09-03T12:40:49+00:00",
"label": "Tag",
"color": null,
"body": "subscriber",
"slug": "subscriber"
}| Field name | Field type | Description |
|---|---|---|
id | string | The visitor unique identifier. |
created_on | string | The timestamp in UTC when the tag is created. |
changed_on | string | The timestamp in UTC when the tag is changed. |
label | string | Type of resource. For tags, this value is Tag. |
body | string | The value of the tag. |
Schema events don’t contain a payload.
Response
View the full list of notifications sent to your webhook on the Webhook detail page in your Prepr account. From here you can view the response the Prepr server received from your endpoint.

Your endpoint must respond with a 2xx status code within 12 seconds. Any other status code or a
request timeout is treated as a failure and triggered for a retry.
If your webhook continues to fail multiple times in 24 hours, your webhook will be disabled. The account owner and any Technical contact users will be notified in this case.
Check out the options below on how to handle responses with errors.
Retry behavior
Prepr attempts multiple times to deliver a given notification to your webhook endpoint with an exponential back off. You can configure a maximum number of retries. If your endpoint has been disabled you can still expect to see future retry attempts.
Disable behaviour
Prepr will actively notify the account owner and any Technical contact users when the webhook is misconfigured or the error rate is 100%. The email also states when the endpoint will be automatically disabled.
View attempts
To manage an existing webhook, go to Settings → Webhooks and click the specific webhook in the list. All attempts of this webhook of the last three days can be viewed and retried here. You can also view the response the Prepr server received from your endpoint.
Resend webhooks
You can resend a webhook event by clicking the icon.
Disable webhooks
You can easily switch off your webhook temporarily. Go to Settings → Webhooks and click the specific webhook in the list. Switch it off by disabling the Active toggle.
Security guidelines
We recommend you protect the endpoints configured in each webhook. This prevents unauthorized actions on your app.
Authorization headers
When configuring your webhook in Prepr, add an authorization Header with a secret access token only your incoming webhook server knows.
Prepr will send all of the custom headers you added when sending a notification, including authorization. If the values don’t match, you can ignore the request.
Whitelisting Prepr server IPs
You can ensure your app is always communicating with Prepr through one of our IP addresses.
87.233.165.0/26
2001:9a8:0:4b:: 64 bitsWebhook signatures
Prepr will sign the webhook events it sends to your endpoints. We do so by
including a signature in each event’s Prepr-Signature header. This allows
you to validate that the events were sent by Prepr, not by a third party.
Before you can verify signatures, you need to store your endpoint’s ID when creating a new Webhook. Each ID is unique to the endpoint to which it corresponds. If you use multiple endpoints, you must obtain an ID for each one.
Verifying signatures
The Prepr-Signature header contains the full json payload you receive.
Prepr generates signatures using a hash-based message authentication code (HMAC) with SHA-256.
Compute an HMAC with the SHA256 hash function. Use the endpoint’s signing ID
as the key, and use the json payload string as the message.
Compare the signature in the header to the expected signature. If a signature matches, compute the difference between the current timestamp and the received timestamp, then decide if the difference is within your tolerance.
To protect against timing attacks, use a constant-time string comparison to compare the expected signature to each of the received signatures.
Preventing replay attacks
A replay attack is when an attacker intercepts a valid payload and its signature,
then re-transmits them. To mitigate such attacks, Prepr includes a timestamp in
the Prepr-Signature header. Because this timestamp is part of the signed payload,
it is also verified by the signature, so an attacker cannot change the timestamp
without invalidating the signature. If the signature is valid but the timestamp is too old,
you can have your application reject the payload.
We recommend a tolerance of five minutes between the timestamp and the current time. We advise that you use Network Time Protocol (NTP) to ensure that your server’s clock is accurate and synchronizes with the time on Prepr servers.
Prepr generates the timestamp and signature each time we send an event to your endpoint. If Prepr retries an event, for example: your endpoint previously replied with a non-2xx status code, then we generate a new signature and timestamp for the next delivery attempt.